

Data Privacy Protection and Blockchain
 Regardless of whether the data has become an energy source or not, the data has indeed become a raw material for many commodities. At present, there are more than 10 Internet companies with a global market value of over US$50 billion. All the products and services provided by these companies are data. The composition of the data is the core economic value of these companies. At present, only a small portion of the profits of global Internet companies are made. The valuation of most Internet companies depends on the results of modeling and analyzing the data on their platforms based on their respective business models.
Regardless of whether the data has become an energy source or not, the data has indeed become a raw material for many commodities. At present, there are more than 10 Internet companies with a global market value of over US$50 billion. All the products and services provided by these companies are data. The composition of the data is the core economic value of these companies. At present, only a small portion of the profits of global Internet companies are made. The valuation of most Internet companies depends on the results of modeling and analyzing the data on their platforms based on their respective business models.
Further in-depth analysis of the production of these data comes from the individual, that is, the users of these companies themselves, these Internet platforms are nothing more than data porters, nothing more than the data generated by the B-end or the data generated by the C-side, the former including games, video, e-commerce, life O2O platform, etc., the latter is represented by social platforms, but in fact the secret of the success of these companies is not that they own the data, but how they use the data.
There is no doubt that having these data is already a good use of them, allowing these companies to offer better products and services, and ultimately to success, so despite the constant explosion of user data on the Internet platform, privacy issues can not be inciting the legitimacy of the Internet platform for sovereignty over these data, because all the progress that we have seen on the human development of the Internet is almost due to this premise.
In this era, in May 2018, the European Union introduced the General Data Protection Regulation (GDPR). If we fully understand the history of the Internet, we can grasp that the focus of GDPR is not to deny the company to users. Data has legal rights, but rather limits the scope of its use and the more important user claims for these data.
However, since the centralized database always needs human management, the biggest value of the blockchain lies in the consensus governance of the data, that is, all users have equal management authority for the data, so the risk of individual mistakes is firstly eliminated from the operation. Before we saw various comments in the media that the blockchain is a paradox for privacy protection, the biggest argument is that the writing of block data requires transparent verification across the entire network, so data privacy cannot be protected. We have reason to believe. The authors of these arguments lack sufficient understanding of encryption techniques represented by homomorphic encryption and zero-knowledge proofs, so it is assumed that transparent verification of the entire network must be obtained with the most primitive data. Just like we are dealing with SERO (a blockchain platform that supports zero-knowledge proof of protecting data privacy), we often encounter similar problems. We often need to spend a lot of time explaining the zero-knowledge proof. Magically allows the verifier to confirm the authenticity of the data (often representing an asset) without knowing the original data.
Zero Knowledge Proof (ZKPs): ZKP is a cryptographic technique that is a zero-knowledge proof that proves certain data operations without revealing the data itself, allowing both parties (certifiers and verifiers) to prove a certain The proposal is real and there is no need to disclose any information other than it is true. In cryptocurrency and blockchain, this usually refers to transactional information data.
Through the network-wide consensus of the blockchain to solve data decentralization, and using zero-knowledge proof to solve the verification problem, it can solve the scenario that the privacy data can be applied even in the open decentralized system, so that it is fully consistent. At the same time as the needs of the Internet platform, some of the data is still only in the hands of users.
Unlike existing Zcash, Monero and other anonymous currency public chains, SERO is not positioned to create only a digital currency that can be used to pay for anonymous assets, but rather to target smart contract programming that supports Turing’s completion, hopefully and in the block. The chain supports richer data structures (such as data structures like Ticket and Package) and even beyond the data types supported by ERC721, in the latest release of BetaNet Release (https://wiki.sero.cash/zh/Index.html?file=News/Release/SERO-BETANET-R1), we have implemented some of these features. After adding the anonymous package asset, almost all data types saved in the current Internet database can be saved and used in the SERO blockchain ledger. Token, Ticket, Package and other types of assets constitute the ecology of the SERO system’s anonymous assets. These asset types are perfectly integrated in a set of coding systems. The programming and development of these assets are combined with the Turing-complete intelligent contracts of the SERO system. The DApp can be creatively implemented in the chain to implement various privacy protections that are not possible on the previous system, and is applicable to the implementation of various business requirements in the field of privacy protection.
Finally, we found that although we did not solve the original intention of the traditional centralized internet platform to solve the privacy protection problem of personal data, we also gave a centralized Internet user data privacy when solving the problem of blockchain network data privacy. A great solution for protection.
We can envisage that some users will be regarded as private data (such as the user’s real name, age, citizen number, asset account, etc., especially those that can link the publicly available data with the real real identity) into the encrypted ledger. Blockchain, the rest of the data can still be located in a centralized server, the platform can verify the user’s true identity validity without knowing its original identity, and can use this data for calculations (such as KYC or content recommendation) to continue to provide better service.
To give a more specific example, in a financial platform, users choose to encrypt sensitive data including citizenship number, specific age, current assets (such as stock market value held) in the blockchain, and some other investments. The preference can be kept by the financial platform, and the platform needs to confirm that the user is over 18 years old, the assets are in the range of 5 million to 10 million, and recommend the financial products that meet the investment tendency of the user, then the system can be realized by SERO. Architecture. At the same time, when the CSRC needs to investigate the true identity of all users who invest in a certain product, the user can provide the SFC with a privileged key, combined with the data on the SERO and the data in the financial platform, so that the CSRC A collection of raw data can be obtained to achieve its statistical purpose.
Sometimes the platform recommends content to users rather than simply determining the range of user data, depending on the user model belonging to the company’s trade secrets, such as the need for a set of encrypted data stored in the blockchain
The last case is for larger data, limited by the current network storage and communication conditions, and the amount of data stored and processed in the blockchain is limited. Therefore, SERO plans to combine multi-party secure computing (MPC) technology in 2019, so that individuals can choose to keep some data in their own terminals, only when they need to be processed in the chain or in the chain contract. The need to participate in the calculation of data communication, which will further extend the scenario and versatility of data protection while achieving data privacy protection.
In any case, SERO has become one of the most powerful solutions for privacy protection solutions in the global blockchain. Unlike many projects with only white papers and schedules, SERO always insists on the latest white papers after the product release. So SERO has become a solution that can be applied directly, not just a future choice.
Users are the creators of data. As the trend of data assetization becomes more and more obvious, the future creation and circulation of individual values will further increase the proportion in the entire economic circulation. We can see the rapid rise of shared taxis and Weibo in recent years. Platforms, knowledge sharing, social networking and other platforms are all based on the creation and circulation of individual economic values. We believe in the development of basic technologies such as blockchain, VR or artificial intelligence, and high-speed development of wireless communications, will be the founder of this trend. In the early years, the development of the human economy experienced the efficiency of economic operation through centralized coordination organizations. With the regularization of the management experience of these industries, the improvement of information dissemination efficiency, and the original pursuit of individual fairness in return on value investment entering the next new era, an economic market dominated by individual value creation, whether it is production or consumption.
Related news
Search news
Recommended news

Super Zero Protocol (SERO) Smart Contracts Tutorial — Issue Anonymous Tokens
2019-05-21
SERO Privacy — Use Cases
2019-05-15
SERO VS Zcash : A comparative analysis
2019-03-31
Is SERO affected by Zero Knowledge Proofs Infinite Counterfeiting Vulnerability?
2019-02-08
Data Privacy Protection and Blockchain
2019-01-17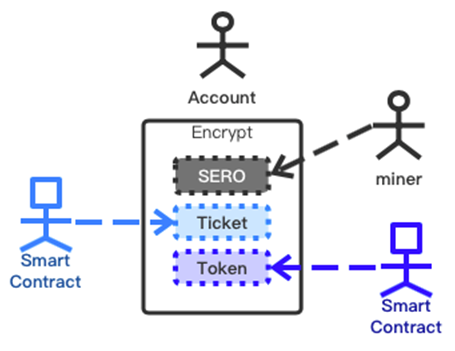
SERO — The Technological Innovation in the Blockchain Privacy Protection
2018-12-17
Privacy Protection and Blockchain
2018-12-15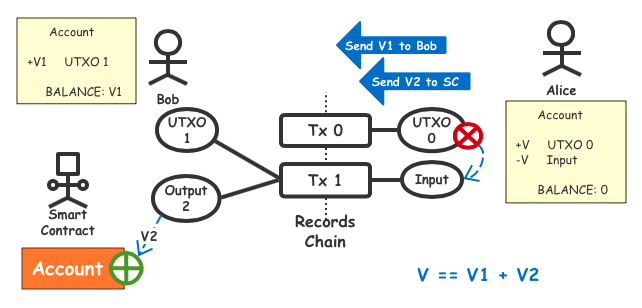
Super Zero Protocol (SERO) Smart Contracts Anonymous Tokens Issuance Principle
2018-12-04