

SERO — The Technological Innovation in the Blockchain Privacy Protection
SERO is a privacy protection platform that uses non-interactive zero-knowledge proofs. SERO is not only the world’s first privacy cryptocurrency to support smart contracts, but also the world’s first development platform that allows developers to issue anonymous tokens that support smart contracts and can be used in DApps. SERO system represents the world’s leading zero-knowledge proofs practice in blockchain privacy protection applications. Because of the unique and powerful technology system of SERO, SERO won the “Blockchain Technology Innovation Award 2018” at the recent 2018 Block China Summit (CHAIN-PLUS+). The following paragraphs will elaborate the outstanding features of SERO system in technical innovation.
Necessity of Blockchain Privacy Protection
As an emerging technology, the core value of blockchain lies in decentralization compared with centralized system. Traditional companies with independent databases should aggregate data and build data centers. In this situation, the management authority of these data centers are all in the hands of a company. Such systems are controlled by a small number of people and have unavoidable problems in terms of security. The blockchain is a chained data structure in which data blocks are sequentially connected in a chronological order, and cryptographically guaranteed non-tamperable and unforgeable distributed ledgers. On the other hand, in the blockchain systems, anyone with the ability to establish a node can participate in it and become a node of the distributed ledger. These nodes are equal and autonomous, participate in verifying each transaction and determine the consistency of data through certain pattern of consensus. Through the blockchain system, users can securely trade and interact with various types of data without the need for intermediate nodes.
For example, in the Ethereum network, there are tens of thousands of nodes around the world, including nodes that users run to promote inter-network projects, nodes that are managed by the exchange, and nodes that miners run. So many nodes, on the one hand, ensure the security of each transaction, on the other hand, it does bring a lot of privacy problems to users. At present, anyone can query every transaction from the tens of thousands of nodes, including the address and amount of the transaction participant. In this situation, how to protect the privacy of the user?
Since the development of the blockchain industry, several privacy protection solutions have been explored in the technical field, such as the coin mixer, the ring signature and the zero-knowledge proofs. The coin mixer is a centralized solution that requires a centralized blending platform. The trading participants first send the tokens to the blending platform for mixing to disrupt the connections between the participants. Users need to fully trust the centralized processing system. Ring signature is a special group signature. The signature of a transaction is generated by a private key and a number of public keys. When other nodes verify the signature, they can only determine which public key is one of many public keys, but cannot locate which public key is the specific sender, that is, it is impossible to locate who is the specific holder of the asset represented by a group of ring signatures. The problem with ring signatures is that the set of signatures used for anonymity is fixed, and the user still needs to mix with other users’ public keys in the transaction, so it is still possible to encounter malicious users and expose privacy.
The most promising one in the blockchain industry is the zero-knowledge proofs, which was proposed by S. Goldwasser, S. Micali, and C. Rackoff in the early 1980s. It refers to the certifier being able to believe that a certain assertion is correct without providing any useful information to the verifier. The zero-knowledge proofs are essentially an agreement involving two or more parties, that is, a series of steps required by two or more parties to complete a task. The prover proves to the verifier and make him believes that he or she knows or owns a certain message, but the proving process cannot disclose any information about the proved message to the verifier. A large number of facts have proved that zero-knowledge proofs are very useful in cryptography. If zero knowledge proofs can be used for verification, many problems can be effectively solved.
In the area of blockchain privacy protection, zero-knowledge proofs are considered to be the most cutting-edge solution and also the most powerful. The founder of Ethereum Vitalik Buterin has repeatedly expressed his appreciate for zero-knowledge proofs in public. In the past, if you want to prove something, you need to introduce or use another knowledge to achieve the goal, but in the zero-knowledge proofs, the user does not need other underlying data to complete the proofs process. In blockchain transactions, users did not need to add or disclose more information to complete the entire transaction process.In a transaction, the transaction process can be encrypted, but other users do not need to decrypt it except for the participants. After the application of zero-knowledge proof technology in blockchain system, only encrypted hash data will exist in each block, which is enough to support the transaction operation on the blockchain system.
However, the problem we are now facing is how to apply zero-knowledge proofs as a universal solution in a wide range of blockchain systems. One of the more outstanding problems is that the efficiency of generating proofsis relatively low. For example, in Zcash, it usually takes hundreds of seconds to send an anonymous currency transaction with an ordinary laptop. If there are more sources in the UTXO in the sent transaction, then the proof time-consuming of the transaction is longer and unbearable. Another problem is that none blockchain platform systems that support smart contracts like Ethereum have emerged in all the current mainstream anonymous currency systems.
In order to solve these problems in the application level of anonymous blockchain systems, many R&D teams are attempting to make further improvements. However, due to the level of zero knowledge proofs and the complexity of its academic and engineering aspects, most teams have made slow progress and have not developed a system that can actually goes online.
The SERO project successfully solved the above problems. SERO is the meaning of Super Zero. It is the world’s first blockchain-based platform that implements privacy protection based on zero-knowledge proofs technology and supports Turing’s complete smart contracts operation. In the term of zero-knowledge proofs system, the SERO team built the Super-ZK zero-knowledge proofs encryption system based on zk-SNARKs. At present, the Super-ZK system is more than 20 times faster than Zcash’s current system in the proofs generation speed, which is the biggest bottleneck of zero-knowledge proof popularization and application, which greatly improves the user’s experience and improves the scope of zero-knowledge proofs system’s practicality.
The architecture design of the SERO anonymous system
The architecture design of SERO anonymous system follows the following basic principles while meeting the system capability requirements.
Un-traceable — every transaction in the blockchain network has an input and an output; constructing an acyclic graph of transactions, on which all of the transaction flows can be tracked, all of the transaction sequences can be concatenated and traced. SERO is designed to break the link between the two transactions, making the attack impossible.
Un-associable — each user in the blockchain network has their own collection address. Once the address is associated with the real user identity, all the transactions occurring at the address in the network can be associated with the corresponding user identity, resulting in the exposure of the associated behaviors to the address. All the transactions and balances are still publicly visible when a user creates a new pseudonym public key for anonymity. SERO uses encryption technology to make the payment address unrelated.
Anti-statistical analysis — actual user behavior has statistical characteristics. If the transaction data in the blockchain network has a correlation that reflect such statistical characteristics, it is possible to deduce the addresses belongs to a specific user through statistical analysis of the blockchain data. When ring signatures are used, the ability to resist statistical analysis will decrease if ring members or nodes are malicious. SERO must be able to completely hide the address and the relationship between addresses by technological means.
Optional auditing solution — for the alternative audit scheme and certain complex business applications, the user may choose a trusted third-party to conduct financial audit of transactions. The user should have the ability to give the third-party to track the specific information from the transactions.
The design of the SERO protocol is briefly described as follows:
Account System
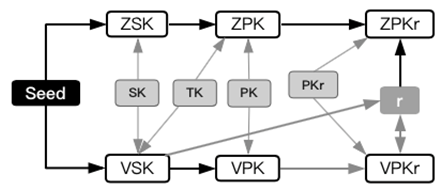
Accounts are divided into two categories: user account and contract account.The user account is a 32-byte
selected by the user, the contract account generates a 64-byte address corresponding to the smart contract environment which the user installed; both categories are unique and non-repeatable.
The user account can generate a 64-byte private key SK and a 64-byte public key PK, as the user’s payment address. When installing or invoking the smart contract, the wallet will generate a temporary address
according to the current condition. The temporary address cannot be associated with the user’s private key and public key and will only be used once.
When the smart contract is installed, the wallet will change the temporary address to a 64 byte smart contract address (CADDR) in accordance with the current condition. As the node receives the address, it needs to ensure that the contract address has not appeared before.
Assets System
User account or smart contract account, has the attribute of managing unlimited variety of assets. With the exception of the settlement of transaction fees using SERO coins,each asset has the same transaction characteristics as SERO coins. Excluding SERO coins, the remaining assets can be generated by a smart contract. Each asset can be given a name of up to 32 byte length (token name) for mnemonic purposes and these names are also not allow to be reused. The asset type can be specified when the account performs balance queries or transfer operations.
Output and Input construct
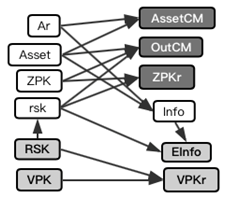
Output construct
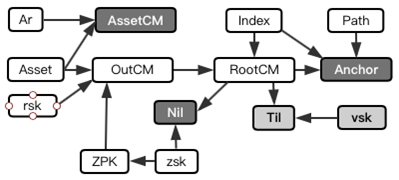
Input construct
Anchor is the root of the Merkle Tree where the input data is located. Nil isthe hash of 32 Byte for destroy the used OUT, Til is the hash of 32Byte for transaction trace, and is only valid for an OUT within the system. AssertCMis the asset commitment of the input. OutCMis the output commitment of the transaction
Witness System
SERO protocol uses non-interactive zero knowledge proofs (NIZK) and needs to provide witness information of assets source when generating transactions. Each node will verify according to the witness information. SERO uses the Merkle Tree to maintain a witness system that records status changes. The system will provide verification function at the nodes and authentication information at the wallet side.
ROOT=MerkelRoot (POSITION, LEAF, PATH)
ROOT is the root of the current Merkle Tree.
LEAF is the leaf at this position.
PATH is the proof path from LEAF to ROOT
Prove System
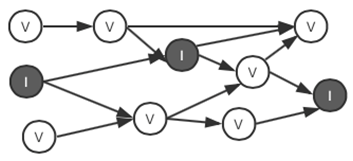
SERO’s prove system includes a calculation circuit based on directed acyclic graph to describe the internal constraints of each SERO transaction: input and output balance of various asset types, verification of public and private key, validity of commitments, validity of witness, etc. The circuit loaded with data can generate a PROOF through non-interactive zero knowledge proofs ( NIZK). From the submission of the PROOF, nodes can verify various parameters and constraints loaded in the circuit while hiding a large amount of detailed information.
Process Step
A. Compute
The user uses the information provided by the account, assets and witness system, and provides input data according to the current required calculations. The calculation rules run under off-chain environment to obtain RESULT
RESULT=COMPUTE(METHOD, ACCOUNT,DATA,WITNESS)
B. Prove
The user generates STX with the random variable r and the result of compute,and submits it to the node. The STX include check-datas Ci, encode-datas Ei and proof-datas Pi.
STX=PROVE(RESULT,r)
STX={(C0. C1……Cn), (E0, E1……En), (P0, P1……Pn)}
C. Verify
After receiving the STX , the node confirms Ci in the witness system and the proof system. When certificates are verified as correct, the node will accept the STX.
RET_i=VERIFYi(C_i)
Check=ret_0 ret_1…ret_n
D. Confirm
As the asset receiver synchronizes to the verified transaction STX, the receiver uses the private key to decipher the encode-datas E_i and generate plain text D_i. The plain text D_i and proof P_i are input to the proof system for verification; success indicates the transaction is validated. When the transaction is confirmed by n blocks, the transaction recipient considers the transaction has been confirmed.
D_i=FETCH_i (E_i,ACCOUNT)
ret_i=CONFIRM_i (D_i,P_i)
Check=ret_0 ret_1…ret_m
It should be noted that the execution steps of SERO are open, which means that such abstract description of steps and parameters can support continuous upgrading and subsequent addition of functions has little impact on the overall architecture.
Super-ZK, the world’s fastest Zero-Knowledge Proof encryption library
For the blockchain system adopting the non-interactive zero knowledge proofs ( NIZK ) scheme, the biggest application bottleneck at present is that the time for generating proofs at transaction is too long. The zero knowledge proofs module Super-ZK of SERO system have made the following breakthrough innovation for this bottleneck.
1. Currently, we use the zk-SNARKs framework to generate NIZK, which uses the ALT_BN128 curve and the Groth16 pre processing process, which reduces the computation time by 1/3 compared with Zcash’s PGHR13 pre processing scheme.Although the zk-SNARKs framework requires a credit installation process, computing circuits will not be dynamically constructed in the SERO implementation, so the zk-SNARKs framework can meet the SERO requirements in all current scenarios.
2. We innovatively use a Twisted Edwards curve written by ourselves to replace the SHA256 hash to generate the public key, and Pedersen Hash to generate the Merkle tree, which can increase the transaction speed by more than 4 times.
3. Compared to the circuit structure of Zcash dual input and output, SERO adopts a single input and output structure, and each description is linked by an asset channel. Such a circuit configuration is more complicated, but in the case of multi-core CPU, Zcash has higher execution efficiency than Zcash.
4. Part of the code of Super-ZK code is written in assembly language. Compared with C++ implementation of Zcash, it has higher execution efficiency.
Based on the above optimization, we have a speed increase of more than 20 times compared with Zcash in the speed of transaction proofs generation, which greatly improves the applicability of the NIZK system.
The Principle of Smart Contract Issuance and Operation of Anonymous Assets
1. The Models of UTXO and ACCOUNT Model
The blockchain is a distributed ledger, the smallest unit of the ledger account is record, and each record stores the inflow or outflow of the account’s assets. According to the different ways of asset outflow recording, the blockchain systems have evolved into two different accounting implementations, which are UTXO model and ACCOUNT model. These two modes correspond to the models of Bitcoin and Ethereum respectively.
The advantages of UTXO model is:
A. Each transaction in UTXO model is independent of each other, which means that transactions under one account can be processed in parallel as long as the problem of double spend can be handled properly, and the capability of multi-core CPU can be fully utilized.
B. UTXO is essentially a record form based on history, both a process and a result, so it has great advantages in some applications where proofs need to be generated. This is why the blockchain systems with CT(Confidential Transactions) features are basically UTXO mode.
The advantages of ACCOUNT model is:
A. ACCOUNT model directly add or subtract the assets in an independent account, and can add or subtract any value of assets in an account with only one record. Therefore, the generated record size is much smaller than the record generated by UTXO in the same situation.
B. The ACCOUNT model is state-based, “Input” and “Output” are processes, and “ACCOUNT” is the result, so it is easy to implement the Turing machine, that is why the blockchain that supports Turing’s complete smart contracts mostly uses the ACCOUNT model.
2. SERO’s Hybrid Model
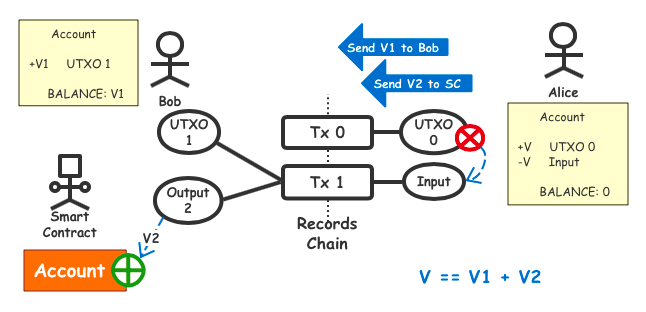
SERO applies UTXO and ACCOUNT models together, using UTXO model where CT(Confidential Transactions) are required, and using ACCOUNT model where smart contracts need to be run. SERO seamlessly integrates these two models through trading, consensus, and Pedersen Commitment algorithms, enabling smart contracts to perform surprisingly.
3. Structure Supporting Anonymous Transactions with Smart Contracts
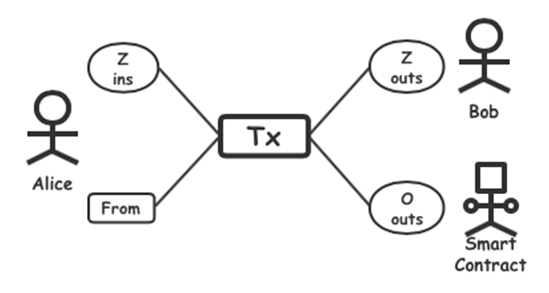
A. Transactions “Tx”
SERO’s confidential transactions “Tx” have an anonymous input set “Z ins”, an anonymous output set “Z outs”, a normal output set “O outs”, and a temporary address “From”. “Z ins” is completely anonymous, making it impossible for third-party observers to find out the source and content. “Z outs” is completely anonymous “UTXO”, only the receiver can view and use its content, the content carried by the “O Outs” is not hidden, and it refers to the receiver in two situations: one is pointing to a smart contract address, and the other is pointing to a temporary address. “From” represents the sender of the transaction and is also a temporary address. Therefore, the whole “Tx” cannot make the third-party observers determine who is the real user, and the information such as assets carried in it is also hidden to the greatest extent.
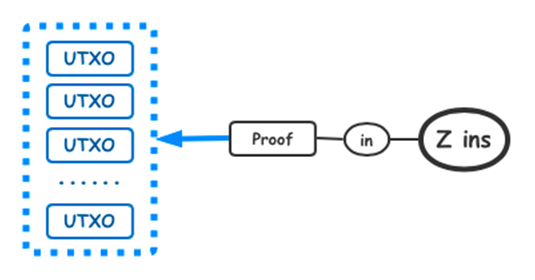
B. Input “Z ins”
In the input set “Z ins” of the SERO transactions, each input is anonymous, including the ID of the source “UTXO” and the asset information carried. Each input is converted to a “Proof” generated by zero-knowledge proofs “ZKP”. The “Proof” pointed to a particular “UTXO” hidden in a huge “UTXO” sequence, which is part of the SERO history, all details hidden by “Proof”. The verifier can confirm whether the input is valid by “Proof” without knowing the details.
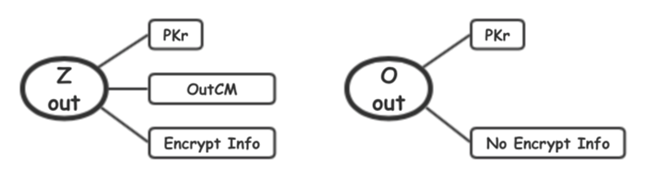
C. “Z outs” Output and “O outs” Output
“Z out” points to the temporary address “PKr”, and the temporary address can only be decrypted by the receiver. Since each temporary address is different, no third party can identify the “Z out” real point address. “Z out” also carries the encrypted information “Encrypt Info” of the asset, which can only be decrypted by the party holding the receiver’s private key. And “OutCM” is the output commitment, only the parties of the transaction can reproduce the computing process of “OutCM”. “OutCM” plays a crucial role in proving that “Z out” is referenced by “ins”.
The PKr pointed to by “O out” has two forms, one is initiated by a smart contract and points to the temporary address of the common account. The other is initiated by a normal account, pointing to the address of the smart contract. Due to the randomness of the temporary address, the third party cannot know the identity of the receiver.
D. The “Balance” of inputs and outputs
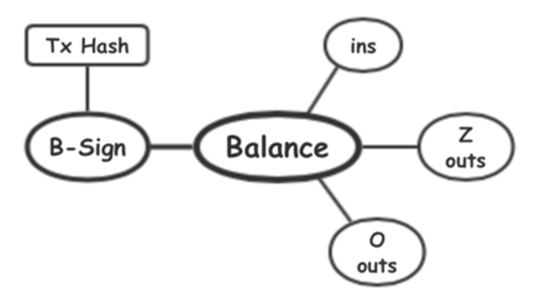
“Tx” packages “ins”, “Z outs”, and “O outs” together. How to prevent malicious attackers from tampering with the data and ensuring asset security? By introducing Perdesen Commitment, its homomorphic encryption feature enables verifiers to confirm that “Balance” must be balanced without knowing the details of the information, that is, the input is equal to the output.
In addition, in order to prevent malicious attackers from tampering with “O outs”, we use the random feature of Perdesen Commitment to sign “Tx Hash” with the random part of “Balance”. In this way, each input and output can be computed independently and then packaged together by “B-Sign”.
E. Transaction Sender “From”
When the output of a transaction points to a smart contract, the smart contract sometimes needs to output resources to a given account based on the written rules. At this time, the temporary address “From” is the place where the output resources are received. “From” is determined when the transaction is generated and used only once. Other than the sender of the transaction, the third parties cannot locate the identity of the sender.
F. Issuance of Anonymous Tokens
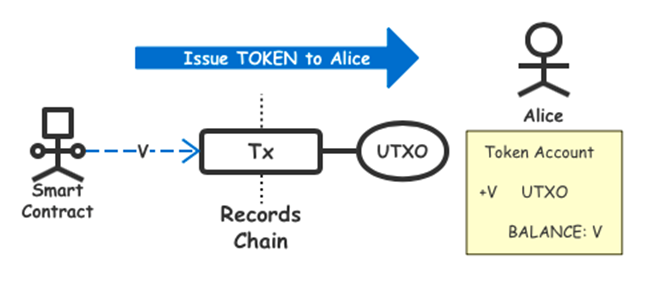
Token, also known as the “homogeneous pass”, is an asset form recognized within SERO system. The same kind of tokens can be arbitrarily divided and mixed. Tokens on SERO system is different from Ethereum’s tokens. As the first currency of the SERO system, SERO coins are also a type of tokens in essence.For Token assets, except for handling fees, which can only be paid in SERO coins, they are treated the same within the SERO system, and their privacy and security are ensured by consensus.Once the anonymous Tokens are successfully issued, the smart contract can send the tokens to the temporary address “PKr” of a normal account in the form of a normal transaction. At this time, these sent tokens will be separated from the smart contract account in the form of UTXO, and transfer into the user’s account like SERO coins , thus being protected by SERO’s privacy mechanism.
G、Issuance of Anonymous Tickets
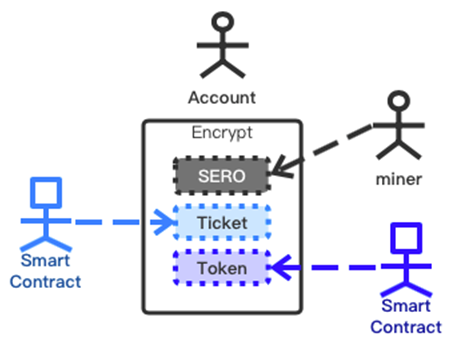
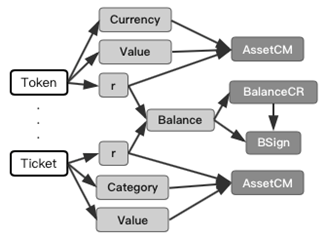
Tickets, also known as the “homogeneous pass”, is another more extensive asset form recognized within SERO system. Different from tokens, tickets are an inseparable form of assets that is unique to the individual.Like tokens, SERO also provides anonymity support for Tickets.When anonymous tickets are issued, the tickets are represented as an ID that are sent as the normal transaction to an account’s temporary address “PKr”, and the tickets are pulled separated from the smart contract account as UTXO and protected by SERO’s zero-knowledge proofs privacy mechanism in a mechanism similar to SERO coins and tokens.
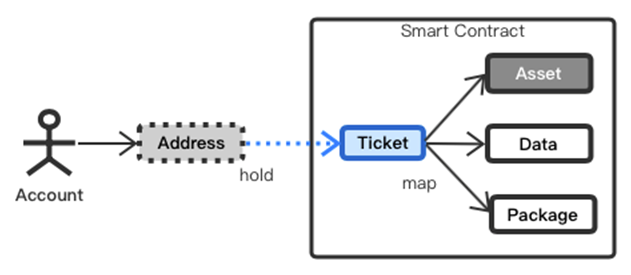
Ticket is a 256-bit digit that can point to complex data structures stored in smart contracts, so it is suitable for the construction of complex business scenarios. A concise example of the data structure pointed to ticket is shown in the figure above. “Asset” is the data structure of an asset. The data structure of this asset can be SERO coin, token or ticket. Because Ticket is directional to data, this structure can support unlimited nesting and form a complex assets structure that meets business requirements. Data can store data encoded by other data structures other than assets, and the data structure represented by this data can also be nested. Package holds the assets or data encoded by the user with a key. With the feature of ticket, developers can completely transform complex game applications such as CryptoKitties into anonymous versions.
H. Package: The Mechanism Supported by SERO System for Encrypted Assets or Packets
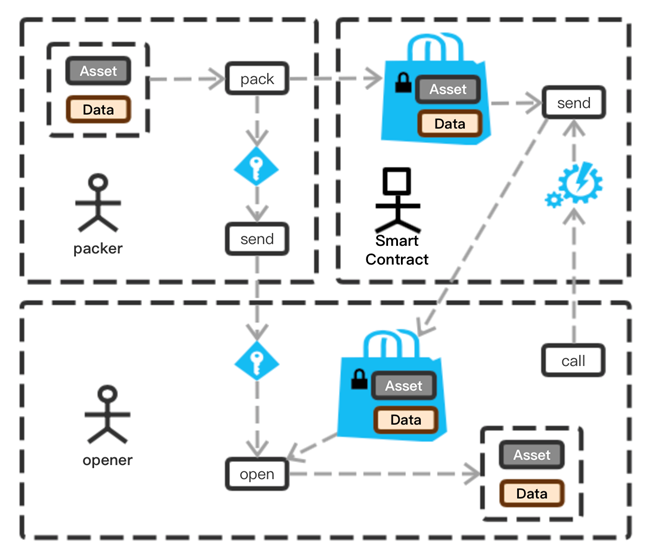
In data-centric applications, these data include timestamps, high-value data storage, various types of proofs data or password strings, asset data, etc. These applications, if implemented in blockchains and input and output by smart contracts, they will encounter exposure problems with plaintext data. SERO also provides the corresponding data protection technology, so that the exposure of these plaintext data is controlled by the user himself. This technology is called Package. The current version of the package uses the symmetrical encryption technology ChaCha20, which is fast and secure. The user can package the Package on the client and get the corresponding key. After packaging, the Package can be transferred anonymously or entered into the smart contract to perform the corresponding logical operation. In the process, the contents of the encrypted package are uncrackable. When decryption is required, the user can privately transfer the key to the associated party according to their own situation, so that the related parties can use the key to decrypt related assets and data.
The four types of assets, SERO coins, Tokens, Tickets, and Packages, together constitute the ecosystem of the SERO system’s anonymous assets. These asset types are perfectly integrated in a single coding system, combined with the programming of these assets by Turing’s complete smart contract of SERO system, developers can pioneer the implementation of various privacy-related DApps that are not supported on the previous system in the blockchain, and are suitable for the implementation of business requirements in various privacy protection fields.
SERO Application Scenarios
Privacy protection is a strong demand for individuals and organizations in the real world. SERO supports Turing’s complete smart contracts and various related privacy components, which can support the expansion of different economic ecology. The issuing of the anonymous asset is no longer exclusive to a few that have extensive knowledge of cryptography. General system developers, with the business needs to issue anonymous cryptocurrency, can issue their own anonymous tokens on the SERO chain and establish their own privacy ecology, therefore, greatly expanding the application of the blockchain systems.Here are some typical use scenarios below.
A. Supply Chain System
The blockchain can solve the problem of upstream and downstream transaction vouchers and traceability of the supply chain system, simplify the management of supply chain central enterprises and providing corresponding solutions for financing of upstream and downstream enterprises. However, sensitive data such as prices and quantity of goods are facing the problem of leaking trade secrets when they are on the blockchain. With SERO system, the problem of exposure to trade secrets can be completely solved, and at the same time, the participating parties can enjoy the benefits brought by the application of blockchain system.
B. Medical Health
Digital privacy is in all aspects of the medical and health industry. From personal medical records to medical treatment records, the multi-role privacy protection and the authorization mechanisms require highly flexible and secure privacy protection capabilities, including hospitals, patients, insurance companies, pharmaceutical companies, etc.The SERO system solves the privacy problems faced by patients and hospitals, and also opens the way for insurance companies and pharmaceutical companies to be safely compliant and use relevant data with the permission of patients.
C. Online Auction
Online auction businesses pursue fairness, the privacy of bids is an important aspect and often difficult to obtain because of conflicting interests. SERO can provide a completely safe, independent and fair bidding environment.
D. Online Casino
The development of online casino industry has always been restricted by the centralization mechanism. The applications of Online casino often require a high degree of privacy protection for competitors’ strategy.In these huge cash flow applications, the decentralized smart contract systems that can provide multiple bids, payment and settlement is needed, and SERO system can fully support this kind of business.
E. Online Gaming
Large-scale online games often need token systems that are easy to circulate, trade and settle, and can be issued and circulate based on smart contracts, while providing privacy protection of transactions. SERO is the only technical solution that supports a multi-token system that issues and circulates homomorphic smart contracts, with added transaction privacy for the accounts.
There are more industries involved in asset digitization and privacy-sensitive digital assets, such as insurance industry, commodities trading, futures trading, credit industry, digital asset trading (such as credit investigation and intellectual property rights, etc.) and so on. In these areas, SERO system has broad application prospects.
Related news
Search news
Recommended news

Super Zero Protocol (SERO) Smart Contracts Tutorial — Issue Anonymous Tokens
2019-05-21
SERO Privacy — Use Cases
2019-05-15
SERO VS Zcash : A comparative analysis
2019-03-31
Is SERO affected by Zero Knowledge Proofs Infinite Counterfeiting Vulnerability?
2019-02-08
Data Privacy Protection and Blockchain
2019-01-17
SERO — The Technological Innovation in the Blockchain Privacy Protection
2018-12-17
Privacy Protection and Blockchain
2018-12-15
Super Zero Protocol (SERO) Smart Contracts Anonymous Tokens Issuance Principle
2018-12-04